Introducing Unified HackerOne Scope Management with Burp Suite Support
We recently introduced Scope Management to the HackerOne platform, which enhances existing functionality to create a unified scope management process across all your organization’s programs on HackerOne. In addition, security testers who use Port Swigger’s popular Burp Suite tool can now download and import their target asset list with a dynamically generated and automatically updated configuration file.
This post will start with the basics of defining scope and how ethical hackers and testers use it in their testing workflow. If you’re already familiar with Burp Suite and the general idea of scope in software testing, skip down and start reading the section that covers Scope Management.
What is a scope?
In penetration testing and bug bounty, scope defines the boundaries of an engagement—what is and isn’t to be included in testing. The purpose of defining an engagement’s scope is to focus testers’ energy on the assets, attack vectors, and vulnerability types that most concern the organization. The organization running the engagement defines the scope, usually with assistance from their vendor or bug bounty provider, to make sure it is accurate.
For example, the purpose of an engagement may be to test a specific, newly-launched application. In that case, the scope would only include that application, with all other assets and infrastructure falling out of scope. Alternatively, an engagement could have a far broader scope that includes a range of critical assets.
A scope can include more than just which assets are to be tested. Bug bounty scopes, in particular, frequently list which testing techniques are (and aren’t) allowed and which vulnerability categories the organization is (and isn’t) willing to pay out for.
What is Burp Suite?
Burp Suite—often referred to simply as Burp—is a suite of tools used to test the security of web applications. The suite integrates basic tools, including:
- Proxy server
- Request repeater
- Scanner
- Spider
- Decoder
- Comparer
…with more advanced tools:
- A Highly flexible fuzzer
- Sequencer
- Multiple extension plugins
- Various automation capabilities
Together these tools support the entire testing process—from initial mapping and analysis of an application's attack surface to finding and exploiting security vulnerabilities. Typical Burp Suite users include penetration testers, internal security teams, and bug bounty hunters.
Defining target scope in Burp Suite
With the scope of an engagement defined, testers will configure a target scope within Burp Suite for each testing project to specify what will and will not be tested. This allows the tester to list which hosts and URLs will be targeted (i.e., attacked) and which will be excluded.
Target scope in Burp Suite is based exclusively on URLs. A URL will only be in scope for a project if it matches something in the include list and doesn’t match anything in the exclude list.
For example, a project may include the URL:
- https://example.com/
And exclude the URL:
- https://example.com/private
In this case, the scope includes everything listed under https://example.com/, including ALL subdirectories—except the contents of the /private subdirectory.
Advanced controls allow you to further define a project’s scope based on each individual component of the URL: the protocol, host IP address, port numbers, and file path.
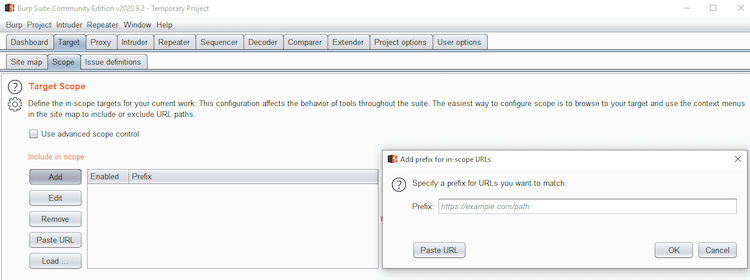
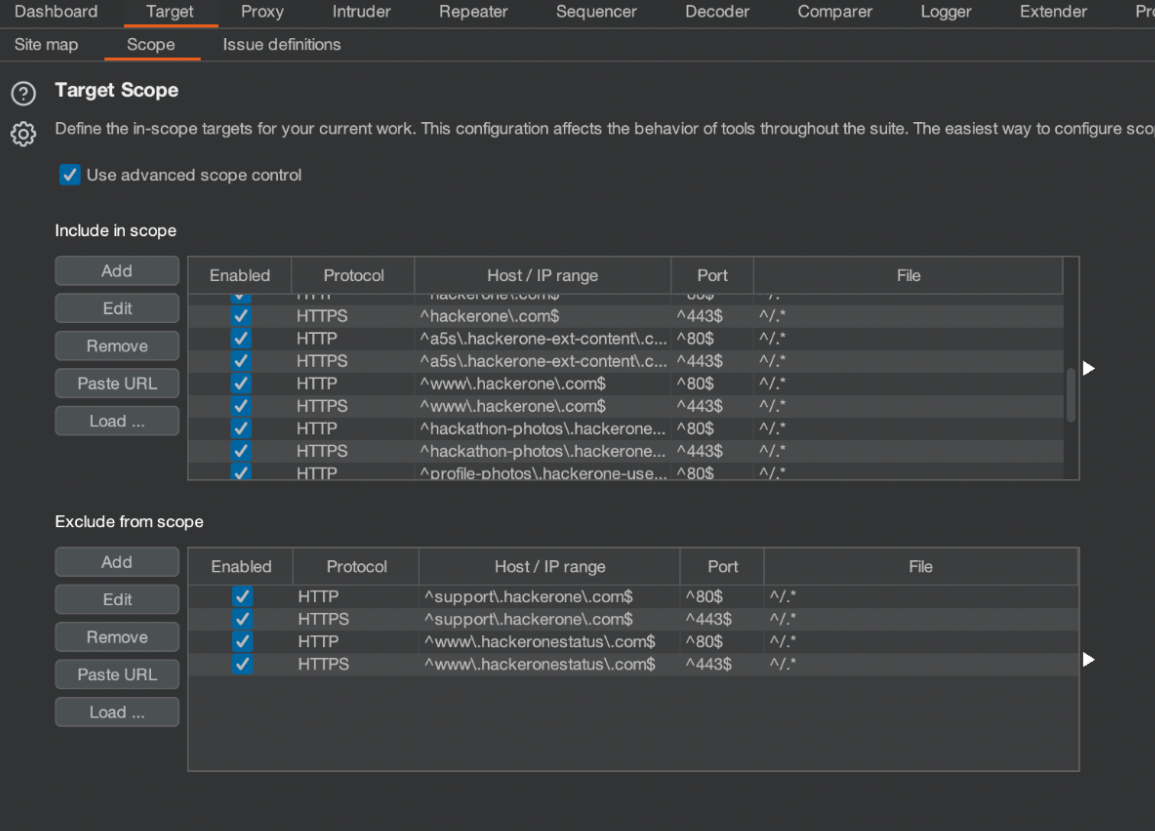
Burp Suite allows testers to manually configure a project’s scope and edit it as needed. Figure 1 above shows how to add target URLs to scope in Burp Suite manually. More details on defining target scope in Burp Suite can be found here.
HackerOne Scope Management
Typically, there is a lot of redundancy in scope management across each pentest, program, and provider that your organization works with. It can be time intensive for a security team to manually track all changes to their organization’s assets and reflect them in the scope of multiple tests. Once your team has taken the time to set the scope accurately, there isn’t an easy way to get that scope directly into testers’ tools.
This is where the HackerOne platform comes in. The new Scope Management feature in the HackerOne platform allows customers to easily manage their bug bounty, Vulnerability Disclosure Program, and pentest scopes from a single interface.
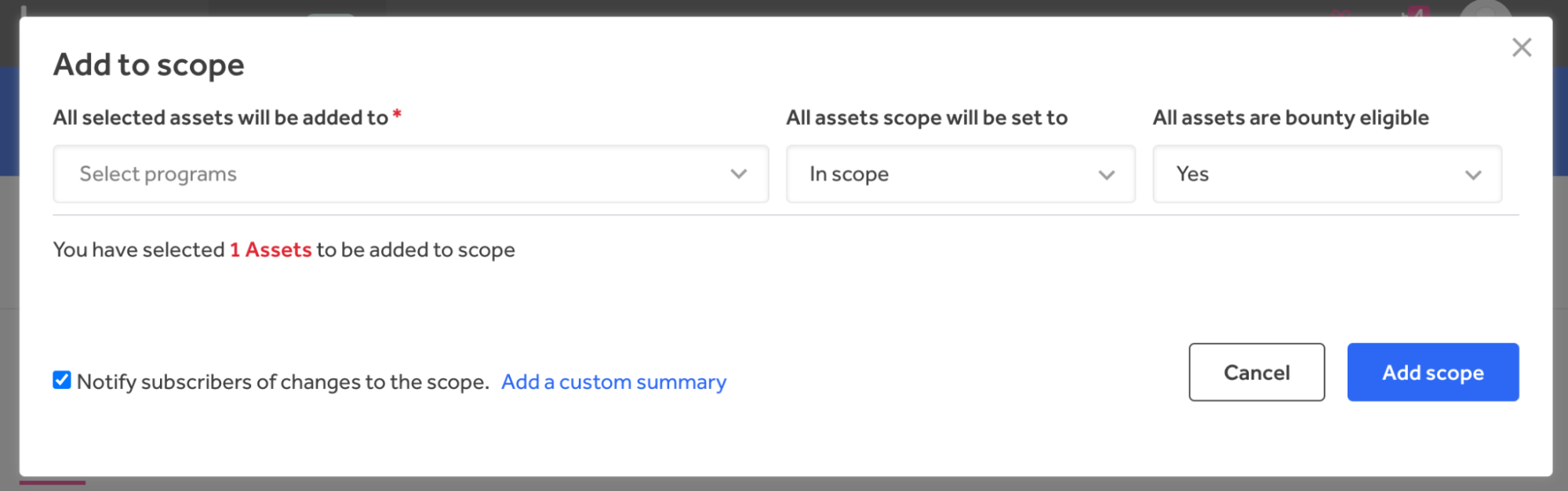
Scope Management allows security teams to select one or multiple assets, add them to active tests, and modify the scope and bounty eligibility via drop-down lists, as shown in Figure 2.
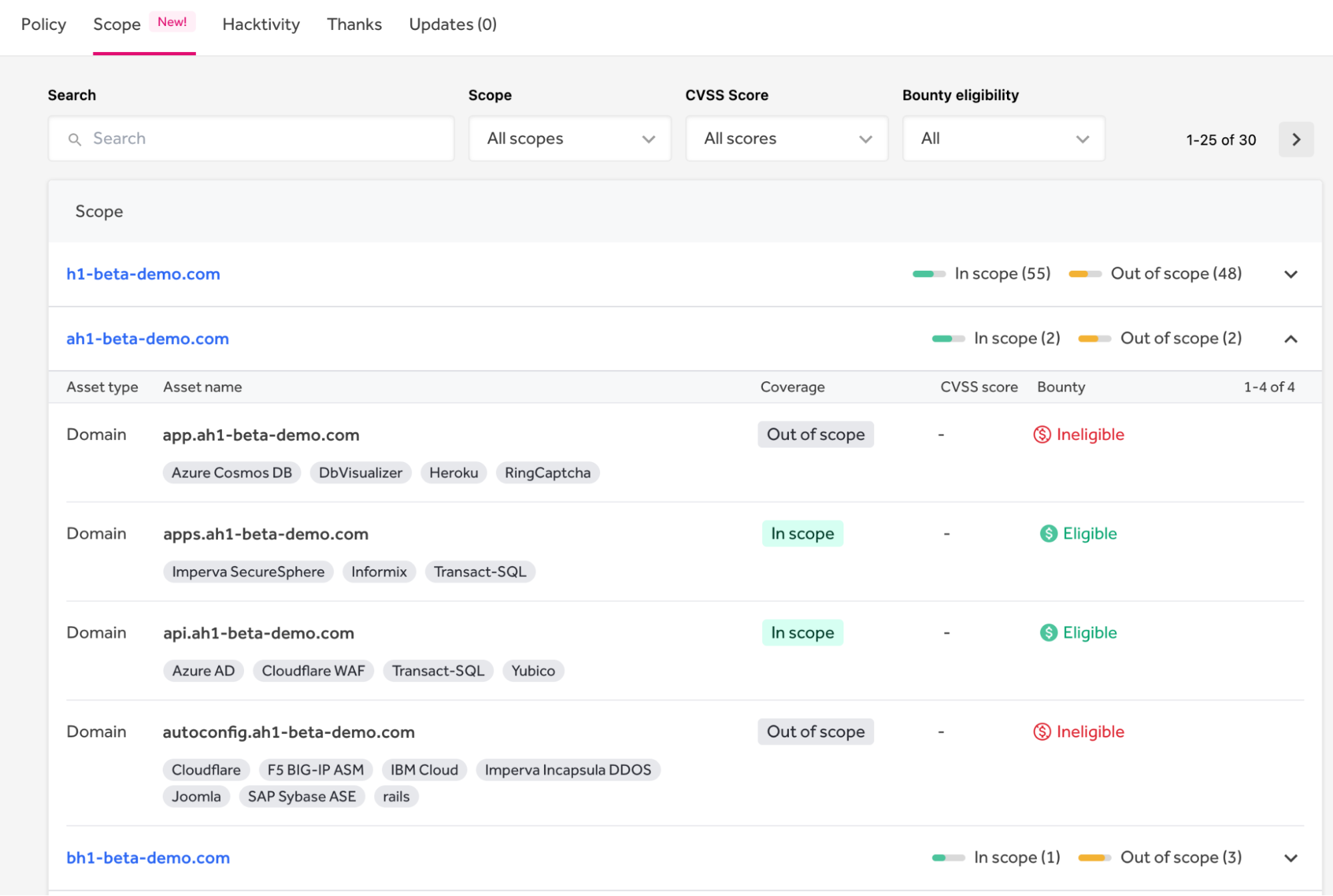
Assets are organized into groups under a single domain. All assets linked to a domain can be viewed by expanding an asset group. Each asset has a type (e.g., domain, URL, IP Address, application, hardware, and many others), a name, coverage (in or out of scope), a CVSS score, and whether it is eligible for bounty. Tags show the technology stack details. For example, as shown in Figure 3 below, api.ah1-beta-demo.com is in scope, eligible for bounty, and uses Azure Active Directory, the Cloudflare WAF, and other technologies.
Automating the creation and maintenance of scope saves time and avoids mistakes. With this enhanced control over scope, security staff can work more efficiently by avoiding the duplication of assets when overseeing multiple tests.
Easily Import Scoped Assets into Burp Suite
Program pages feature a new Scope tab where hackers can view and filter assets that are in or out of scope. This tab increases the discoverability of assets by providing in-platform workflows that enable bounty hunters and pentesters to search and filter a customer’s scope, as seen below in Figure 4. This allows hackers to hone in on the assets and risks they specialize in, even when your scope includes thousands of assets.
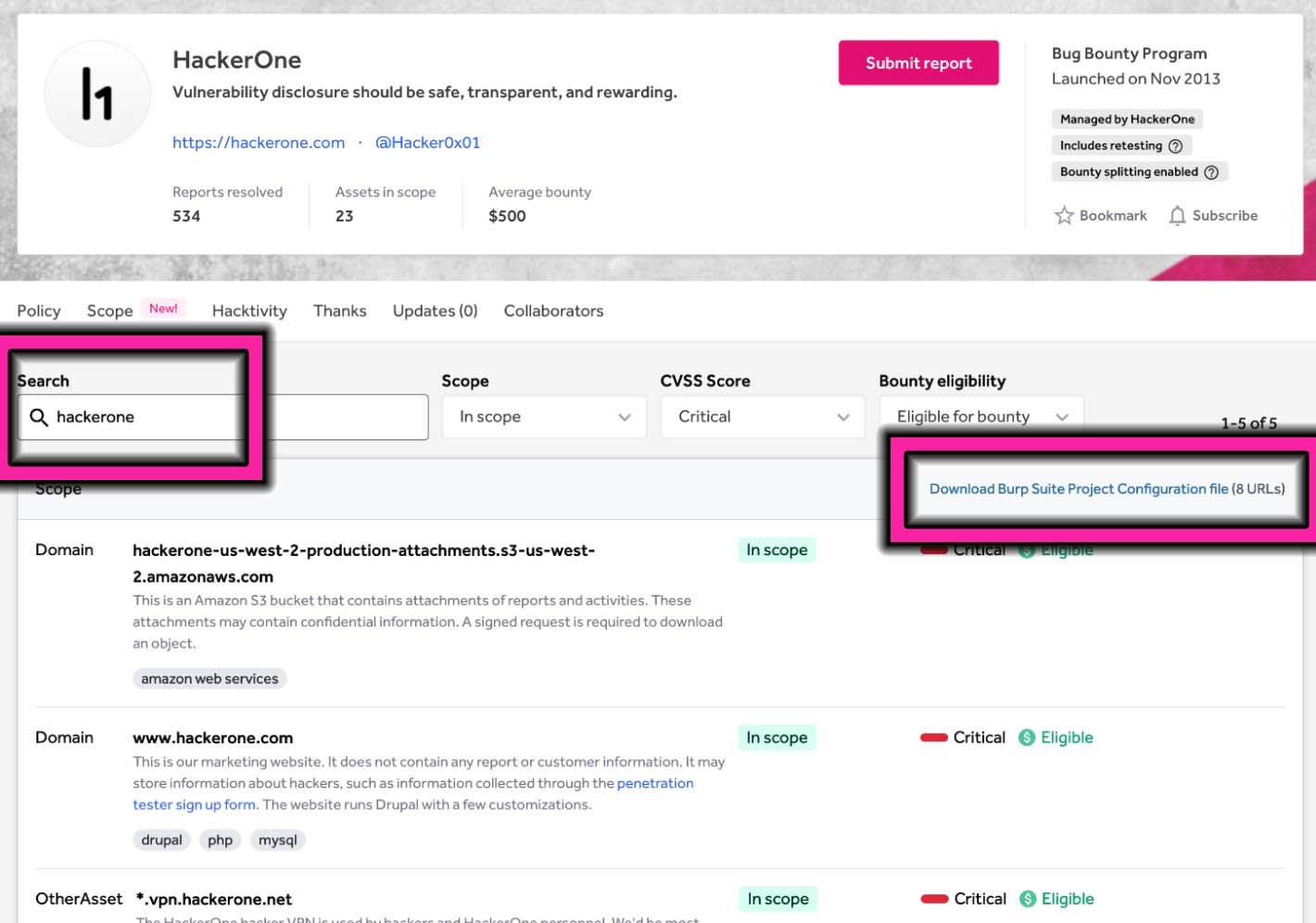
Hackers and testers can filter your scope by CVSS score and bounty eligibility. Then, they can easily import filtered assets directly into BurpSuite with a dynamically generated Burp Suite Project Configuration file, shown in Figure 5. This file contains a list of URLs to be used as the target scope matching the applied filters.
Automating the creation of a Burp Suite Project Configuration file lets hackers start testing more quickly and removes human error when setting it up manually. Figure 6 shows the scope file after it’s imported into BurpSuite. This capability works in HackerOne Bounty and in HackerOne Assets, so pentesters can also take advantage of it.
Scope Management Improves Efficiency and Testing Outcomes
Scope Management improves your organization’s engagements. Security operations staff save time setting up and maintaining scopes for pentests and bug bounty. The new Scope tab helps penetration testers and bug bounty hunters find and understand assets more easily. Finally, automatically updated Burp Suite configuration files speed up project setup for pentesters and bounty hunters working on programs running on HackerOne.
The 7th Annual Hacker-Powered Security Report